Security blogger Brian Krebs wrote recently about how his PayPal account was hacked by cybercriminals through PayPal's outdated authentication processes.
The cheeky hacker called PayPal’s customer service call centre and managed to impersonate Brian (otherwise known as social engineering) and reset his password by providing the last four digits of his Social Security number and the last four numbers of an old credit card account. PayPal has a feature that produces an alert and generates security passcodes for two-factor authentication, but did not require the passcode for a password reset over the phone.
PayPal said in a statement “While the funds remained secure, we are sorry that this unacceptable situation arose and we are reviewing the matter in order to prevent it from happening again”.
Apparently its documented procedures were not followed, which highlights no matter how strong your automated systems are, people and process are still often the weakest link. To be fair to Paypal, they are in the minority when it comes to having implemented a two factor authentication process somewhat successfully and more business have to do this.
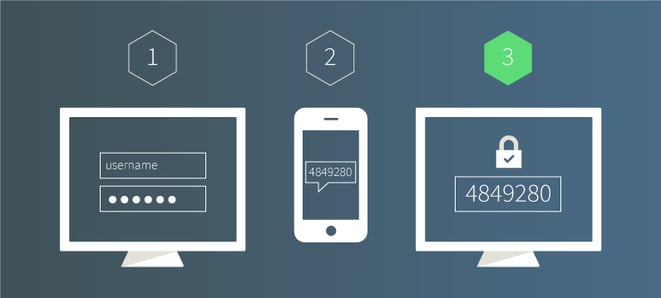
What is two-factor authentication (2FA)? This is the use of two-factors to prove one’s identity. It is based on the premise that an unauthorised actor is unlikely to be able to supply both factors required for access . Authentication uses any two of the following three factors: something you have (ID token, email address, smart phone), something you know (a password) and something you are (fingerprint, retinal scan). For simplicity, 2FA generally requires that you provide something you have (like a phone) on-top of something you know (password) to authenticate.
Consumers are starting to be aware of and demand 2FA – bank regulators are starting to demand it too. Challenge questions (such as your first pet’s name) are no longer enough to provide that second factor because the answers are too easy to find on the Internet. In 2016, we’ll see more banks, online retailers and smart apps adopt mobile authentication.
One approach is to use smartphones to serve as ‘something that the user possesses’ in addition to ‘something the user knows’ like a password. The user identifies themselves via a login and password and the second authentication is provided by a one-off code sent to their phone which is then input by the user.
The use of smart phones as a second authentication factor is also a reminder to utilise good device security measures like automated password phone locks, and ‘find my iphone’ security type measures. Two factor authentication, although more secure, does not alleviate the need for good strong passwords, changed regularly and not given out to any third party – regardless of how credible they seem. As per the PayPal example, users being tricked into supplying passwords or other personal information remain the entry point for most security breaches.
I know for myself, I’ll think very hard about dealing with a business and giving over my credit card and identity details if they haven’t implemented a version of 2FA e.g. mobile. Some great examples of companies who have implemented mobile 2FA are Google, Facebook, Steam, ASB and Amazon. If you haven’t turned on this free feature for your accounts, it’s advisable to do so now!